There is no doubt that social media users are getting younger and for many children and young people, online activity has become a way of life. Unfortunately for our young people the internet has many terrible dangers and poses a real and significant risk to some of the most vulnerable of our society.
What risks do children face?
Whilst there are many dangers associated with internet use, broadly speaking there are seven areas of risk that are commonplace on social media/networking. These are:
- Sexual exploitation.
- Sexting.
- Cyberbullying.
- Criminal Exploitation
- Exposure to pornographic material and violent media.
- Exposure to extremist ideology.
- Serious crime – kidnap, rape and murder.
Whilst these can be considered the most common forms of risk, this list is far from exhaustive. Other potential danger areas for vulnerable young people include: disclosing personal and private information, identity theft, fraud and criminal exploitation.
What is Online Sexual Exploitation?
Online child sexual exploitation can occur through social networking, chat rooms, instant messaging, dating sites and many more platforms. It is an area where law enforcement agencies struggle to keep pace with the methods employed by perpetrators and new developments in technology. Offenders may act alone but also link in with other likeminded individuals, e.g. to share indecent images or extreme pornography. Often the exploitation occurs without the child’s realisation. Exploitation and abuse can take some of the following forms:
- encouraging a child to take part in or perform a sexual activity
- encouraging or asking a child to take and share explicit images of themselves
- encouraging or asking a child to film themselves performing a sexual activity
- grooming
- bullying
- harassment
- baiting (a form of cyberbullying where a victim is accused of sexual promiscuity)
Whilst many of our colleagues are of the view that peer on peer child sexual exploitation is the most prevalent form of CSE, our opinion differs. Our view is that online exploitation is or is becoming the most prevalent form of exploitation. In the USA, it is estimated that 15% of children aged between 10 and 17 have been approached online by a person who has a specific sexual intent. That equates to over 20 million children (NCMEC). Here in the UK it is estimated that one in five 8 to 11-year olds and seven in ten 12 to 15-year olds have a social media profile. Therefore, it makes complete sense to the sexual predator to use a media platform which provides so much exposure to children and one that it is difficult to ‘police’ by those tasked with safeguarding children. Many young people don’t think twice about befriending or having conversations online with individuals they have never met or do not know. We have dealt with several missing children who have in excess of 2000 contacts on Facebook. Whilst this is the extreme, many children have hundreds of online ‘friends’. Identifying who a child might be talking to or associating with online, is therefore very difficult.
Online sexual predators are clever and will use any means they can to identify and target vulnerable young people. An estimated 20% of children who have online social media accounts display private and personal information for all to see, whilst approximately 25% fail to set proper privacy settings on their accounts. Most young people will openly place private information onto their networking site and have at least a profile or cover picture of themselves on their social media page. Many others will have hundreds of photos available to be viewed by anyone. Most social networking sites contain location services and what may appear to be innocent posts make it easy for online predators to identify potential victims within their area or in places they are prepared to travel to. The emergence of GPS location technology which is available on most smartphones makes it even easier for online offenders to target and locate vulnerable young people. Some can identify where a photograph of a young person was taken, simply by downloading software which can pinpoint within several metres or so, the location the image was captured.
It is clear there is a growing trend for children to take sexualised (nude/semi-nude) photographs of themselves which they then share with another person or people online. Whilst for many children this is a voluntary action, many other children are bullied, blackmailed and coerced into taking and sharing inappropriate images of themselves. Whether it is a voluntary act or not, once an image is shared and posted it becomes difficult to have it removed from a social network sight. If it is then taken from the media site and posted on the wider internet then there is no way to remove it – what goes online, stays online.
Once an image falls into the hands of an offender then the child can become more susceptible to being blackmailed into taking part in, or performing sexual acts. Whilst this can involve online sexual predators, evidence suggests that this an area of offending where the perpetrators are the victim’s peers. It is becoming commonplace for images to be shared between mutual groups and the victim being referred to as ‘Sket’ amongst their peers. The term ‘sket’ is a derogatory slang term for a promiscuous girl or woman with a bad reputation.
It is likely that a young person will not recognise the coercive nature of the relationship the perpetrator(s) has formed with them, and therefore will not see themselves as being a victim of exploitation. The young person may well believe they are in a consensual loving relationship and their loyalty will be to the abuser. Fear of being discovered, fear of the perpetrator, shame and embarrassment are some of the reasons that a young person might steps to prevent a parent, carer or other responsible adult from discovering the extent of their online activity.
Some indicators that a young person has developed an unhealthy online relationship:
- takes steps to conceal the device or change passwords and security settings
- hide the screen when disturbed unexpectedly
- refuses or is secretive about who they are communicating with
- spending excessive amount of time online
- online time substantially increased
- have become obsessive about being online
- become withdrawn, angry and upset after communicating online
- become over the top happy after communicating online
- their social media profile(s) has become more sexualised or contains darker content
- their profile has changed, and they appear to adopt an older persona or a different persona
- are communicating with or have an older group of friends on their social media site
- have dropped their usual social media friends
- are using multiple email accounts
- are visiting sites that are unhealthy, i.e. self-harm sites, extremist
If it wasn’t difficult enough spotting whether a child is being targeted online, a savvy young person will know how to hide or delete their browsing history and will often have email or social media accounts that parents, or carers are unaware of. They can also get plenty of help online to aid them in their deceit. Web anonymisers are websites that allow a user to surf the web without leaving a footprint. They use a proxy server that acts as an intermediary between the user’s device and the rest of the internet.
There are also many apps on the market commonly known as ‘Photo Vaults’ which are apps that look like innocent productivity apps such as a calculator. In fact, behind the disguise is a hidden vault that have complex password systems and allow a young person to hide all those video, images and texts that they don’t want a parent or carer to discover.
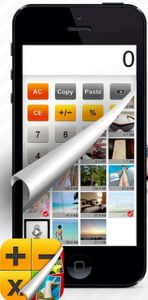
Some ‘photo vault’ apps include:
- Keepsafe Private Photo Vault
- Vault-Hide
- Secret Calculator
- Don’t Touch
- KYMS vault
- Secret Apps – the Locker
- Keeper